When a cloud strategy is developed, it is very important to
include data protection. As more and more enterprise applications move to
cloud, only the resilient cloud infrastructure is not enough as corruptions,
accidental deletion etc. can still happen and backup must be included in the
cloud strategy.
Most cloud providers provide native snapshot functionality
however snapshots are not the same as backup. Snapshots are not application
consistent and do not support granular recovery.
The Dell EMC Networker with CloudBoost solution provides
optimized data protection for enterprise applications regardless of whether
they are running on-premises or in public cloud. Here are the various use
cases.
Here I am going to share more about “Backup in the Cloud”, where Enterprises have workloads running in
the public cloud virtual machines (here AWS EC2) and would like to use public
cloud object storage (here AWS S3) to store the backups.
Solution Components
Networker is a
unified data protection software solution for the enterprises that centralizes,
automates and accelerates backup and recovery across multi-platform
environments, both physical and virtual.
CloudBoost is a
data protection-optimized cloud enabler for use on-premises and in the cloud.
It employs source-side encryption,
compression, deduplication and WAN optimization for highly efficient
backup in the cloud.
AWS S3 is
a highly scalable, reliable, fast, inexpensive object
storage provided by AWS.
While testing this, I have used public cloud infrastructure
provided by Amazon Web Service (AWS). Our production servers/VMs are running as
EC2 instances in a private subnet in AWS VPC and have Networker client
installed. These being the Linux clients, the backup data will directly flow to
object storage (AWS S3) and only meta-data will go to Networker Server and
CloudBoost Appliance.
In this demo, Networker server and CloudBoost appliance are
also installed in private subnet. Public subnet hosts a jump host for external
users to connect and a NAT gateway.
All the production VMs (EC2 instances) required to be backed
up, which are running in private as well as public subnet. With this, let us
start configuration tasks and test backup and restore of EC2 instances to S3
Bucket.
High level Steps:
- Install and Configure Networker Server and clients on EC2 instances
- Deploy the CloudBoost appliance from EC2 AMI
- Register and Configure CloudBoost appliance in the EMC Cloud Portal
- Configure Networker to work with CloudBoost appliance
- Perform Test Backups
- Perform Test Restore
1. Install and Configure Networker Server and
clients on EC2 instances
It
is assumed that Networker Server and Clients are already installed and
configured as per standard procedures on EC2 instances. Make sure that EC2
instance has sufficient role assigned to write to S3.
2. Deploy CloudBoost appliance from EC2 AMI
Use the CloudBoost AMI to launch an EC2 instance of size m4.xlarge in Private subnet of VPC. Also make sure that
require ports are opened in the Security Group and this instance can connect to
DellEMC Cloud Portal on port 443 and EC2 instance has sufficient role assigned
to write to S3.
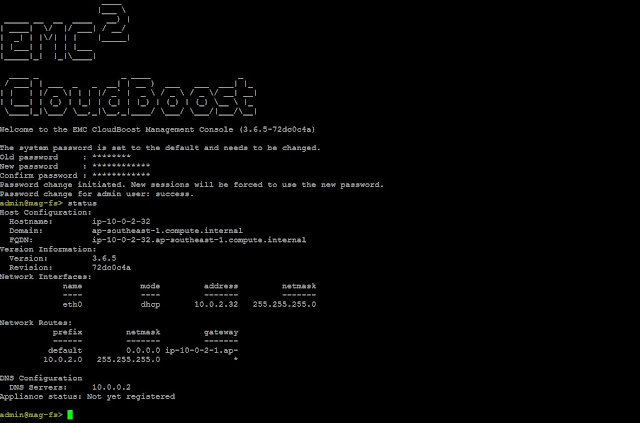
Once
deployed, ssh to CloudBoost and verify the status
Change Hostname and other details if required
admin@mag-fs> fqdn
cloudboostappliance.ap-southeast-1.compute.internal
*
Processing request
*
Changing hostname
*
Restarting DHCP
*
Restarting configuration controller
*
Restarting configuration agent
*
Restarting statistics collection service.
FQDN changed successfully
admin@mag-fs> status
Host Configuration:
Hostname:
cloudboostappliance
Domain:
ap-southeast-1.compute.internal
FQDN:
cloudboostappliance.ap-southeast-1.compute.internal
Version Information:
Version: 3.6.5
Revision: 72dc0c4a
Network Interfaces:
name mode address netmask
---- ---- ------- -------
eth0 dhcp 10.0.2.32 255.255.255.0
Network Routes:
prefix netmask gateway
------ ------- -------
default 0.0.0.0
ip-10-0-2-1.ap-
10.0.2.0 255.255.255.0 *
DNS Configuration
DNS
Servers: 10.0.0.2
Appliance
status: Not yet registered
admin@mag-fs>
3. Register and Configure CloudBoost appliance
in the EMC Cloud Portal
Login to DellEMC Cloud Portal and create a Cloud Profile pointing to the
AWS account by entering proper Region, AWS Access Key ID and Secret. This shall
create the required Bucket in the given AWS Region to store the backup data.
Register the CloudBoost appliance using the
claim code generated via CLI
admin@mag-fs> register
Please use claim code XXXXXXX to register this
device with the cloud controller.
Waiting for console to claim the code
.............
Appliance successfully registered.
admin@mag-fs>
Enter the claim code in the Cloud Portal
and verify the status
admin@mag-fs> status
Host Configuration:
Hostname:
cloudboostappliance
Domain:
ap-southeast-1.compute.internal
FQDN:
cloudboostappliance.ap-southeast-1.compute.internal
Version Information:
Version: 3.6.5
Revision: 72dc0c4a
Network Interfaces:
name mode address netmask
---- ---- ------- -------
eth0 dhcp 10.0.2.32 255.255.255.0
Network Routes:
prefix netmask gateway
------ ------- -------
default 0.0.0.0
ip-10-0-2-1.ap-
10.0.2.0 255.255.255.0 *
DNS Configuration
DNS
Servers: 10.0.0.2
Appliance status:
Registered, Not yet configured
admin@mag-fs>
Once registered, it will be visible on Cloud
Portal
Configure the appliance by providing necessary
information as shown below
Once completed, verify the status
admin@mag-fs> status
Host Configuration:
Hostname: cloudboostappliance
Domain: ap-southeast-1.compute.internal
FQDN:
cloudboostappliance.ap-southeast-1.compute.internal
Version Information:
Version:
3.6.5
Revision: 72dc0c4a
Network Interfaces:
name mode address netmask
---- ---- ------- -------
eth0 dhcp 10.0.2.32 255.255.255.0
Network Routes:
prefix netmask gateway
------ ------- -------
default 0.0.0.0 ip-10-0-2-1.ap-
10.0.2.0 255.255.255.0 *
DNS Configuration
DNS Servers: 10.0.0.2
Appliance status: Initial configuration completed
4. Configure Networker to work with CloudBoost
appliance
Set the remote mount password on the CloudBoost to be used for backup
admin@mag-fs>
remote-mount-password enable YOURpassword
100% done. Status: Password
changed successfully
Changing remote mount
password: success
admin@mag-fs>
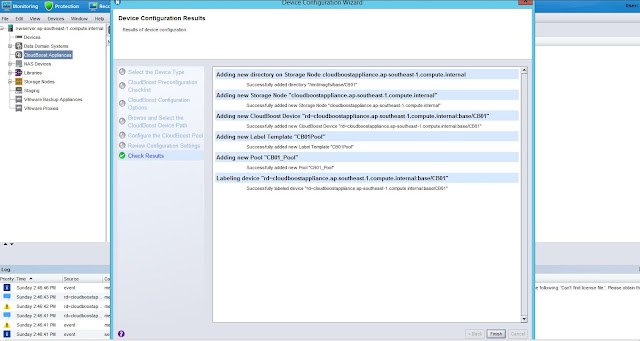
Use Device Configuration Wizard in Networker NMC to configure CloudBoost
Device as below
You can
verify that couples of S3 Buckets are created with their names starting with “mag”
5. Perform Test Backups
Configure
the Networker Policy and Workflow to backup to new Pool created above which
uses CloudBoost Device
Start
the Workflow to run the backup
Query
the savesets and verify the Media Type
As these backups are using Source Deduplication, you can see the space savings
and dedup ratio on Cloud Portal
6. Perform Test Restore
Let
us perform a test restore from the backup just taken
Here is
the successful restore
As we saw, NetWorker and CloudBoost solution enables data
protection for enterprise applications running in the public cloud, on-premises
in the data center or both.
Hope this is helpful!